OAuth
Theory (OAuth 2.0)
OAuth need 3 part in the concept :
- Resource owner : Give authorization
- Authorization server : Give Token
- Resource server : Give Ressource
There is different way to ordinate it
Authorization Code Grant
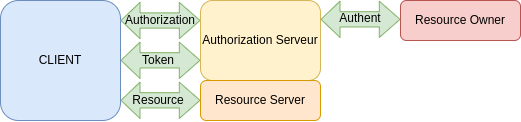
The Client ask for authorization > the owner have said ok to the Auth Server > the Auth server say ok to the client > the client ask for a token > the Auth server give the token > the client ask for content to the ressource server > if good token the server give the ressource
Implicit Grant
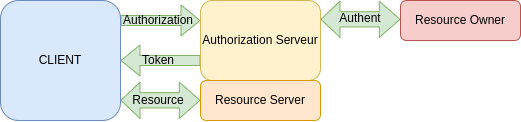
The Client ask for authorization > The Auth server check if the owner said ok > The Auth server send the token to the client > The client ask for the Resource to the Resource server > If token ok the Resource server send the resource for the client
Attacks
Mechanics
Redirect
In SSO-like login there may have a parameter in the request like “redirect_uri” where there is the reference to the “SSO” service and it’s where the token wil be send.
If this parameter isn’t safe we can’t put our own server and sometimes it just checked the first character or if there’s the domain so it’s possible to do redirect like this :
http://legitim.safe.malicious.hack/
http://legitim.safe@malicious.hack/
http://malicious.hack/callback?a=http://legitim.safe
http://malicious.hack/callback#http://legitim.safe
State is fucked
Missing
The state parameter is a nonce to ensure the id of the person answering to us is the right one.
So if the state is missing we may infiltrate the communication from the victim by puting our token instead of his and force him to log into a malocious account.
Not checked
State parameter can be used for XSS by injecting JS into it.
# Normal
curl http://legitimate.safe/login?state=23THA3Z456YJE
# Malicious
curl http://legitimate.safe/login?state=23THA3Z456YJE"><script>alert(1)</script>